A Global Censorship Prison Built by the Women of the CIA
Is building a slave state for Big Daddy the apex achievement of feminism?
By Elizabeth Nickson | Welcome to Absurdistan | May 18, 2024
The polite world was fascinated last month when long-time NPR editor Uri Berliner confessed to the Stalinist suicide pact the public broadcaster, like all public broadcasters, seems to be on. Formerly it was a place of differing views, he claimed, but now it has sold as truth some genuine falsehoods like, for instance, the Russia hoax, after which it covered up the Hunter Biden laptop. And let’s not forget our censor-like behaviour regarding Covid and the vaccine. NPR bleated that they were still diverse in political opinion, but researchers found that all 87 reporters at NPR were Democrats. Berliner was immediately put on leave and a few days later resigned, no doubt under pressure.

Even more interesting was the reveal of the genesis of NPR’s new CEO, Katherine Maher, a 41-year-old with a distinctly odd CV. Maher had put in stints at a CIA cutout, the National Democratic Institute, and trotted onto the World Bank, UNICEF, the Council on Foreign Relations, the Center for Technology and Democracy, the Digital Public Library of America, and finally the famous disinfo site Wikipedia. That same week, Tunisia accused her of working for the CIA during the so-called Arab Spring. And, of course, she is a WEF young global leader.
She was marched out for a talk at the Carnegie Endowment where she was prayerfully interviewed and spouted mediatized language so anodyne, so meaningless, yet so filled with nods to her base the AWFULS (affluent white female urban liberals) one was amazed that she was able to get away with it. There was no acknowledgement that the criticism by this award-winning reporter/editor/producer, who had spent his life at NPR had any merit whatsoever, and in fact that he was wrong on every count. That this was a flagrant lie didn’t even ruffle her artfully disarranged short blonde hair.
Christopher Rufo did an intensive investigation of her career in City Journal. It is an instructive read and illustrative of a lot of peculiar yet stellar careers of American women. Working for Big Daddy is apparently something these ghastly creatures value. I strongly suggest reading Rufo’s piece linked here. It’s a riot of spooky confluences.

Intelligence has been embedded in media forever and a day. During my time at Time Magazine in London, the bureau chief, deputy bureau chief and no doubt the “war and diplomacy” correspondent all filed to Langley and each of them cruised social London ceaselessly for information. Tucker Carlson asserted on his interview with Aaron Rogers this week that intelligence operatives were laced through DC media and in fact, Mr. Watergate, Bob Woodward himself, had been naval intelligence a scant year before he cropped up at the Washington Post as ‘an intrepid fighter for the truth and freedom no matter where it led.’ Watergate, of course, was yet another operation to bring down another inconvenient President; at this juncture, unless you are being puppeted by the CIA, you don’t get to stay in power. Refuse and bang bang or end up in court on insultingly stupid charges. As Carlson pointed out, all congressmen and senators are terrified by the security state, even and especially the ones on the intelligence committee who are supposed to be controlling them. They can install child porn on your laptop and you don’t even know it’s there until you are raided, said Carlson. The security state is that unethical, that power mad.
Now, it’s global. And feminine. Where is Norman Mailer when you need him?
At the same time, at the same time, Freddie Sayers, the editor-in-chief of Unherd, testified in Parliament on the Global Disinformation Index which had choked Unherd’s ability to grow. Unherd had hired three advertising firms who were, one after the other, unable to place ads. The third sourced the problem to the Index, which had deemed his interviews with journalist Katherine Stock about the problems faced by young people transitioning their sex, had made him persona non grata for all advertising agencies across the world. Eerily, that same week, Katherine Stock was awarded a high honorable mention in the National Press Awards for her work.
Here is Clare Melford, the fetching chief of the Global Disinformation Index, a woman seemingly bent on sterilizing confused children, Yet another non-profit authoritarian working for a mysterious Big Daddy. Who the hell trained her?

On Tuesday this week, out pops Europe’s headmistress, European Commission President Ursula von der Leyen in Politico.eu, complaining about “Russia” and “right-wingers” sowing distrust of Europe’s election processes. She is, she says, launching a new war on Disinformation. Most importantly, no more reporting on migrant assaults. This seems to be their new crusade. Please note the halo over her Christed head. Honestly, they are shameless, vain, silly creatures with limited bandwidth. Other than obedience to some grim reaper.

Said Politico :
“She promised to set up “a European Democracy Shield,” if reelected for a second term, to fight back against foreign meddling.
EU cybersecurity and disinformation officials expect a surge in online falsehoods in the 20 days prior to the European Parliament election June 6-9, when millions of Europeans elect new representatives. Officials fear that Russia is ramping up its influence operations to sow doubt about the integrity of elections in the West and to manipulate public opinion in its favor.”
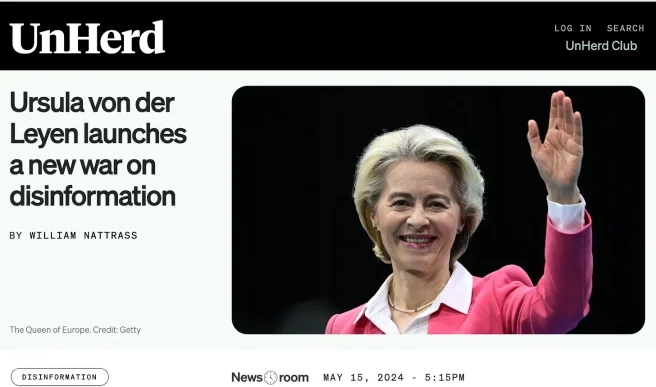
By the way, madam, western election integrity has been thoroughly compromised by the men who tell you what to do. More than half of us think elections are stolen. More than half. That’s not disinformation, it’s math.
This week Michael Shellenberger, who is the acknowledged lead in the take-down of the global censorship complex, had a look at Julie Inman Grant, another American Barbie, now Australia’s “e-safety commissioner,” with ties to the WEF. Grant had demanded that X censor a migrant stabbing, and X refused. Grant, as Shellenberger describes, is the Zelig of internet history tinkering in the bowels of said internet until she burst onto the public stage as Australia’s chief censor, bent on building a global online safety network.
Working for Big Daddy is apparently something these ghastly creatures value.
At a recent government hearing, she announced, “We have powerful tools to regulate platforms with ISP blocking power, and can collect basic device information, account information, phone numbers and email addresses, so that our investigators can at least find a place to issue a warning.” Grant went on to say they could compel take-downs, fine perpetrators and fine content hosts.
The Daily Mail had a ball with Inman Grant, mocking her and pointing out that she was wasting taxpayer money on a game of whack-a-mole.

Nevertheless, Grant takes herself very very seriously and since she is accreting power at a massive clip, so must we.
Grant’s network of independent regulators is called the Global Online Safety Regulators Network. “We have Australia, France, Ireland, South Africa, Korea, the UK and Fiji so far, with others observing. Canada is coming along,” she preens, “and is about to create a National Safety Regulator.” Canada’s proposed censorship program is so draconian you can be jailed for something you posted online years ago. And the government proposing it is so unpopular, it will be lucky to hang onto 20 seats in the next election.
There are literally hundreds of these women. Why? Why?
At a meeting this year of the World Economic Forum, Věra Jourová, from the European Commission, outlined just how exciting she and her team found the tools she is being given. “We can,” she said, “influence in such a way the real life and the behavior of people!” She sighed with excitement after this sentence. Jourova was caught last September trying to spread yet another Russia hoax. You have only to hear censorship plans uttered in a central-European accent to really understand what is happening here.

As terrifying as this all seems, and it is terrifying, it is instructive to look at the ruination of the career of America’s chief censor, Renée DiResta. DiResta, as research head of the Stanford Internet Observatory, is now being sued for abuse of power and unethical behavior that violates the constitution. Spookily, DiResta soared from “new mom” to providing the intellectual under-pinnning for censorship, until she headed up the Stanford Internet Observatory during Covid, where she was instrumental in censoring vaccine and Covid “disinformation.” People thought her backstory contrived and in fact, Shellenberger found that she was, unmistakably another CIA trained censor of inconvenient information under the guise of “safety.”
At this point, every time you hear the word ‘safety”, it’s best to check your ammunition supply. Said Shellenberger:
As research director of Stanford Internet Observatory, DiResta was the key leader and spokesperson of both the 2021 “Virality Project,” against Covid vaccine “misinformation” and the 2020 “Election Integrity Project.”
Shellenberger goes on to look into DiResta’s work history and finds a lot of congruence with CIA operations.
But then I learned that DiResta had worked for the Central Intelligence Agency (CIA). The journalist Matt Taibbi pointed me to the investigative research into the censorship industry by Mike Benz, a former State Department official in charge of cybersecurity. Benz had discovered a little-viewed video of her supervisor at the Stanford Internet Observatory, Alex Stamos, mentioning in an off-hand way that DiResta had previously “worked for the CIA.”
In her response to my criticism of her on Joe Rogan, DiResta acknowledged but then waved away her CIA connection. “My purported secret-agent double life was an undergraduate student fellowship at CIA, ending in 2004 — years prior to Twitter’s founding,” she wrote. “I’ve had no affiliation since.”
But DiResta’s acknowledgment of her connection to the CIA is significant, if only because she hid it for so long. DiResta’s LinkedIn includes her undergraduate education at Stony Brook University, graduating in 2004, and her job as a trader at Jane Street from October 2004 to May 2011, but does not mention her time at the CIA.
And, notably, the CIA describes its fellowships as covering precisely the issues in which DiResta is an expert. “As an Intelligence Analyst Intern for CIA, you will work on teams alongside full-time analysts, studying and evaluating information from all available sources—classified and unclassified—and then analyzing it to provide timely and objective assessments to customers such as the President, National Security Council, and other U.S. policymakers.”
At this juncture it is a race, as the intelligence community moves to shut down the revelations of its manipulations and machinations, and people injured by the vaccine and the flagrant abuse of election integrity move to fight them. It is instructive to note that DiResta, while apparently soaring to the heights of journalism at Wired, the New York Times, the Atlantic, selling her safety/censorhip program, cannot seem to get actual people to read or subscribe to her Substack. DiResta, like so many women in power now, are in reality, talentless cutouts for a hidden and malignant agenda.
An agenda that the people of the world roundly hate. I have just one final thing to saw to these truly dreadful human beings. My God is stronger than whatever demon or predator you obey. And as a woman, I am ashamed of each and every one of you. To use one of your awful phrases: Do Better.
Brussels should remember that Europeans are sovereign, not the EU treaties or the Eurocrats
BY GRZEGORZ ADAMCZYK | REMIX NEWS | MAY 17, 2024
In an interview with Tygodnik Solidarność weekly, Prof. Ryszard Piotrowski, a constitutional lawyer from the University of Warsaw, expressed his concerns over the legal challenges posed by the implementation of the European Green Deal. He believes that these challenges threaten the legal identity and autonomy of both the European Union and Poland.
The professor emphasized the foundational role of dialogue in Polish law, noting that European laws are becoming increasingly incomprehensible and detached from the real needs of European citizens.
He argued that the perception of Europeans as subordinates to the European Parliament and the European Council, rather than as sovereigns over the treaties, poses a significant threat. “The sooner we understand that we, as Europeans, are not servants to the treaties and the European Parliament, the better it will be for Europe,” he stated.
He also questioned whether the Green Deal’s objectives align with the Polish constitution, which mandates environmental protection guided by the principle of sustainable development. According to him, the current shape of EU climate policy contravenes this principle by jeopardizing overall economic growth and thereby the security of citizens.
Piotrowski additionally highlighted that the Green Deal threatens essential social rights guaranteed by the Polish constitution, such as housing, energy, and communication security.
“We have a right to energy security, and its violation threatens democracy itself because democracy without a socio-economic dimension is devoid of meaning,” said the professor. Furthermore, he noted that the Green Deal also threatens the principle of subsidiarity, which aims to empower citizens and their communities.
Adding to the urgency of his concerns, Professor Piotrowski pointed out that the implementation of the Green Deal might weaken Poland’s defensive capabilities at a time when a military conflict looms near its eastern border. He criticized Europe’s stance on the conflict in Ukraine, arguing that despite European treaties pledging to promote peace, the current approach could lead to tragic consequences for Europe.
“Contrary to what European treaties stipulate and what they commit Europe to, it has chosen to speak of war instead of striving for peace. Such actions have always ended tragically for Europe,” the professor warned.
Moscow responds to latest EU ban on Russian media
RT | May 18, 2024
Russia’s State Duma chairman has accused the EU of censoring alternative opinions and curtailing freedom of speech, with the goal of deceiving citizens.
Vyacheslav Vlodin was commenting on Brussels’ latest ban on Russian media outlets, which has sparked a warning of countermeasures from the Foreign Ministry in Moscow.
On Friday, the European Council announced it was suspending the broadcasting activities of four additional media organizations, claiming that they “spread and support” Russian propaganda.
The blacklist includes RIA Novosti news agency, newspapers Izvestia and Rossiyskaya Gazeta, and the Czech-based portal Voice of Europe.
Writing on Telegram on Saturday, Volodin described the move as showing the EU’s desire “to close access to objective and reliable information” for residents of member states.
According to the lawmaker, “the policy of double standards has become an integral part of European structures” as they only “talk about freedom of speech, but do not tolerate it in reality”.
Officials in Brussels have no arguments to convince EU citizens that they are right and as soon as they see any problems, they just block “any alternative point of view, destroy freedom of speech, and violate the right to freely disseminate and receive information,” Volodin stressed.
“In fact, they introduce censorship with the only purpose – to deceive their citizens and stay in power,” he argued.
The Russian Foreign Ministry, commenting on Brussels’ move, noted that Moscow has repeatedly warned the EU that “repressive measures” against Russian media will not go unanswered.
“Ignoring these warnings forces us to take countermeasures, which will follow inevitably,” the ministry’s spokeswoman, Maria Zakharova said on Friday.
According to the diplomat, Brussel’s decision is proof “of the neglect by the EU and its member states for their international obligations in the field of ensuring media pluralism and another example of the degeneration of democratic societies” in the West.
Since the Ukraine conflict escalated into open hostilities in February 2022, the EU has barred several Russia-associated media outlets from engaging with audiences in member states. Even hosting content made by the targeted organizations is illegal in the bloc.
Moscow has also taken a harsh stance on Western media. Citing anti-Russian sentiment, misinformation and censorship, the national media regulator has barred access to Twitter, Facebook, Instagram and the websites of the BBC, Deutsche Welle, along with other media outlets.
Labor strike in 10 California universities demands the right to protest for Palestine
Palestinian Information Center – May 18, 2024
Around 48,000 workers at 10 universities affiliated with the University of California system and the Lawrence Berkeley National Laboratory in the state of California, USA, voted to begin a strike in defense of the right to protest for Palestine.
This follows campaigns of arrests and attacks on students in tents, who are demanding an end to the Israeli aggression on Gaza, following the university administration’s failure to address complaints regarding the handling of pro-Palestinian protests.
Activists promised that the union vote on starting the strike next Monday represents a historic decision that may push unions in other universities and labor unions to strike in defense of students’ right to protest for the Palestinian cause.
The announcement of the strike comes two days after the vote of the academic workers at the University of California, where the union considered it a result of changes to the university system’s policies regarding freedom of expression and discrimination in pro-Palestinian speeches, and allowing attacks on protesters during their sit-ins.
In this context, high schools in the state of Wisconsin joined schools in the state of Illinois in student protests at American universities, by walking out of classrooms after the second or third period, and organizing marches inside schools to demand an end to the aggression on Gaza.
Pro-Israeli billionaires fuel NYC Mayor crackdown on Columbia students

Al Mayadeen | May 17, 2024
A coalition of billionaires and influential business figures, aiming to influence American public opinion regarding the Israeli war on Gaza, urged New York City’s Mayor in private last month to deploy police to quell pro-Palestinian demonstrations at Columbia University, The Washington Post reported, citing communications obtained and individuals familiar with the group.
Business leaders, including Daniel Lubetzky, founder of Kind Snack company, hedge fund manager Daniel Loeb, billionaire Len Blavatnik, and real estate investor Joseph Sitt, convened for a Zoom video conference with Mayor Eric Adams on April 26. This meeting took place about a week following the Mayor’s initial dispatch of New York police to Columbia’s campus, as indicated in a log of chat messages.
During the call, some participants discussed the possibility of making political contributions to Adams, as well as strategies for exerting pressure on Columbia’s President and trustees to authorize the Mayor’s deployment of police to address protesters on campus, according to summaries of the chat messages as reported by The Post.
A member of the WhatsApp chat group said, as quoted by The Post, that he “contributed” $2,100, the maximum allowable amount, to Adams during that month.
Additionally, some members expressed willingness to fund private investigators to aid the New York police in managing the protests, as indicated in the chat log. A member reported in the chat that Adams accepted this offer. However, a spokesperson for City Hall claimed that the New York Police Department has not utilized private investigators for managing protests.
Business leaders, Mayor Adams navigate crackdown on US students
 The messages detailing the conversation with Adams were part of a vast collection of WhatsApp exchanges involving several prominent business leaders and financiers across the US. This group includes individuals such as former Starbucks CEO Howard Schultz, Dell founder and CEO Michael Dell, hedge fund manager Bill Ackman, and Joshua Kushner, founder of Thrive Capital and brother of Jared Kushner, who is the son-in-law of former President Donald Trump.
The messages detailing the conversation with Adams were part of a vast collection of WhatsApp exchanges involving several prominent business leaders and financiers across the US. This group includes individuals such as former Starbucks CEO Howard Schultz, Dell founder and CEO Michael Dell, hedge fund manager Bill Ackman, and Joshua Kushner, founder of Thrive Capital and brother of Jared Kushner, who is the son-in-law of former President Donald Trump.
Individuals with direct access to the chat log provided its contents to The Post under the condition of anonymity, as the chat was intended to remain private. Members of the group confirmed the existence of the chat and their contributions.
The chat was initiated by an associate of billionaire and real estate magnate Barry Sternlicht, who opted not to directly participate but communicated through the associate, as indicated in the chat messages and confirmed by a person familiar with Sternlicht, as per the report.
In an October 12 message, one of the initial messages in the group, the associate, posting on behalf of Sternlicht, informed others that the group’s objective was to “change the narrative” in support of “Israel”.
Stretching beyond New York
Formed shortly after October 7, the chat group’s influence has extended far beyond New York, reaching the highest echelons of the Israeli government, the American business sphere, and prestigious universities, The Washington Post reported.
EU Big Brother is Watching News of Fico Assassination Attempt
By John Leake | Courageous Discourse™ | May 17, 2024
According to a report this morning in BNN Bloomberg :
The European Commission said it’s “actively monitoring” the spread of fake news about Wednesday’s shooting Slovak Prime Minister Robert Fico and warned it can slap Big Tech platforms with fines for failing to tackle disinformation.
The regulator “is equipped with wide-ranging investigatory and supervisory powers, including the power to impose sanctions and remedies,” it said in an emailed statement.
Violations could be punished under the European Union’s tough new Digital Services Act, which forces online platforms to put into place measures to tackle illegal content and disinformation, uphold user rights, and protect user’s health and wellbeing.
In other words, the European Commission has already decided the orthodox narrative of this crime—even before a full and transparent investigation has been performed—and will censor any theory or narrative of the crime that diverges from the orthodoxy.
Who Is Juraj Cintula?
Is the man who tried to assassinate Slovak Prime Minister Fico really a “lone wolf”?
By John Leake | Courageous Discourse™ | May 16, 2024
The Telegraph and the Times of India have published profiles on the 71-year-old Slovakian poet, Juraj Cintula, who tried to assassinate Slovak Prime Minister, Robert Fico. The following is from the Telegraph report:
Juraj Cintula, a 71-year-old poet from the western town of Levice, posted online rants against Mr Fico before opening fire on the Left-wing nationalist at close range on Wednesday.
A photo of the writer published on X, formerly Twitter, showed him protesting against the government’s controversial reforms…
[Fico] is viewed as one of the EU’s most pro-Russian leaders after campaigning on a platform to end weapons donations to Ukraine.
In a post for the Movement Against Violence in 2022, Mr Cintula condemned Russia’s invasion of Ukraine. “What Slavic brotherhood?” he wrote, referring to Kremlin claims that Ukraine and Russia could be joined as they were essentially the same country. “He is only the aggressor and the attacked.”
A friend from Levice told Markiza TV that the pair had debates about politics, saying: “I’m more for Russia. He had different opinions.”
In 2015, Mr Cintula founded the campaign group Against Violence and sought to get it officially registered in Slovakia. “Violence is often a reaction of people, as a form of expression of ordinary dissatisfaction with the state of affairs. Let’s be dissatisfied, but not violent,” a petition circulated by him said.
… Unverified video footage emerged on Wednesday of Mr Cintula saying he did not agree with Mr Fico’s “government policy”. In another social media post, he criticised the Fico government for not cracking down on gambling.
The suspect’s political leanings appear to have shifted over time. He was once pro-Russian, and railed against “eyeless gypsies” and migrants before shooting the populist prime minister, who is fiercely anti-migrant.
I was surprised by how quickly the Slovak interior minister, Matus Sutaj Estok, characterized Cintula as “a lone wolf” who “did not belong to any political groups.”
It seems to me that no apparent political group affiliation does not necessarily mean that Cintula was not influenced or directed by someone else. Cintula’s online political rants in which he expressed strong emotions and shifting opinions could have flagged him as man who could be approached and influenced by an agent serving powerful interests. In this hypothetical scenario, Cintula may have fallen under the influence of an agent who presented himself under false pretenses.
Like many other reasonable people, I noticed that Prime Minister Fico has vocally criticized COVID-19 vaccines, endless shipments of weapons to Ukraine, mass immigration, transgender ideology, and climate change ideology. This makes him one of the few heads of state in Europe who has challenged all four articles of faith in what I call the Holy Quadripartitus of Piffle.
1). COVID-19 vaccines are saving mankind. Anyone who questions the safety and efficacy of the vaccines is guilty of heresy.
2). The U.S. proxy war in Ukraine is a sacred mission and no negotiated settlement with Russia shall be countenanced. Anyone who criticizes the Ukrainian and U.S. governments, and any attempt to understand the war from the Russian point of view, is guilty of heresy.
3). Human induced climate change will soon destroy the earth if trillions aren’t spent to overhaul our entire energy policy. Anyone who questions this proposition is guilty of heresy.
4). The concept of biological sex is a mere “construct.” Skilled surgeons and endocrinologists can transform a boy into a girl or vice versa. Anyone who questions this assertion is guilty of heresy.
Given the fervent belief in the Holy Quadripartitus—the Nicene Creed of the vaccine cartel, arms dealers, money launderers, lobbyists, racketeers, and child butchers—it is a matter of certainty that Prime Minister Fico has a vast array of powerful enemies.
UK Army Unit Labeled Accurate COVID Reporting as “Malinformation”
By Didi Rankovic | Reclaim The Net | May 16, 2024
More details are coming out about the Covid-era activity of the UK army unit, the 77th Brigade, which the country’s government used to spy on citizens, suppress dissent around issues related to the pandemic, and flag content for social media sites to label or remove.
The unit, said to be of the psyops (“psychological operations”) variety, carried out a series of controversial and even suspected unlawful activities over this period of time, although in early 2021, the UK government flat-out denied it was involved in “any kind of action against British citizens.”
But a batch of subsequent responses to freedom of information requests, including those filed a year later by the Big Brother privacy-promoting NGO, tell a different story.
Perhaps it’s hardly the fault of the 77th Brigade that it spread disinformation while saying it was fighting it, or that it was among agencies that came up with the idea to get government censors to infiltrate social platforms – after all, the unit was set up in 2015 for the purpose of conducting “covert (online) warfare and subversion campaigns.”
The more pertinent question may be why the UK government decided to rely so heavily on the military (the country’s air force, RAF, was also involved) in order to monitor and censor people’s discussions about things like masks, lockdowns, vaccines – and why these soldiers were instructed to turn on their fellow citizens.
Either way, it did, and it was: In one example early in the pandemic – March 2020 – Guardian reporter Jennifer Rankin tweeted that both UK and EU sources had confirmed the former was not a part of the EU’s PPE procurement project.
The military was quick to label this as “malinformation” – apparently the “code word” for making sure the government is perceived positively regardless of whether reporting/content is accurate. In Rankin’s case, it was.
Big Brother Watch researcher Jake Hurfurt writes about this and cites a whistleblower who revealed how the 77th Brigade managed to bypass legal rules around using the army to monitor dissent at home.
“The leading view was that unless a profile explicitly stated their real name and nationality, which is, of course, vanishingly rare, they could be a foreign agent and were fair game to flag up,” the whistleblower is quoted as saying.
But there’s another way the authorities worked around “the problem,” Hurfurt explains: “As in the United States, UK government officials insist that the flagging of social media content by officials was legal because the officials were just making suggestions, not demanding censorship.”
UK Disinformation Unit Minutes Reveal Consideration of Placing Government Employees Inside Social Media Companies
By Didi Rankovic | Reclaim The Net | May 15, 2024
Recently released minutes from the UK government’s Counter Disinformation Unit (CDU) governing board, the Disinformation Board, provide further evidence of the authorities’ direct involvement in monitoring online speech during the pandemic but also flagging it for removal.
But even this wasn’t enough for CDU, which in 2023, after several years of criticism and scrutiny by some media and privacy groups, got rebranded as the National Security Online Information Team (NSOIT).
One of the moves considered by top UK officials was to “embed” civil servants in companies running social platforms, and it remains unclear if this was in fact done, writes Big Brother Watch’s Jake Hurfurt for Public.
CDU was only one building block in the UK’s Covid-era censorship effort; several military units were enlisted to participate as well, most notably and controversially the 77th Brigade, whose job is supposed to be spreading misinformation, and in general, finding its “psyops” targets abroad, not at home.
NSOIT (CDU) also states that it is “countering disinformation and hostile state narratives.” But these and several other outfits, as well as private contractors hired by the government, were tasked with surveillance of British citizens and suppression of those seen as “Covid measures dissenters.”
And so, what scores of freedom of information requests have since revealed is that they went not after disinformation-spreading “foreign adversary” – but ordinary British citizens, medical professionals, journalists, and even politicians who were engaging in legitimate, albeit critical of the government, speech.
Regarding the lengths to which the UK was prepared to go – specifically if officials actually got “embedded” in social media companies – this is unclear to this day thanks to the government’s refusal to provide access to reports compiled by Logically, a private company.
Logically made millions from contracts with the British military, Hurfurt notes. Completing the picture of the web of sometimes loosely, other times tightly inter-connected entities that work hard to censor online speech, he adds:
“(Logically) has a large US presence and is headed by US ex-intelligence officer Brian Murphy, who worked at the Department for Homeland Security (DHS).”
Meanwhile, the UK government explains its refusal to shed light on the question of whether or not its officials were directly involved with social media companies as fears those reports “would reveal its capabilities to hostile actors.”
Australia jails whistleblowers for telling the truth
By Maryanne Demasi, PhD and Magdalene L. D’Silva, BA/LLB, LLM, MA | May 15, 2024
On May 14, 2024, David McBride, a 60-year-old former military lawyer, was sentenced to five years and eight months in prison with a non-parole period of 27 months, for ultimately blowing the whistle on alleged war crimes committed by other Australian soldiers in 2013.
McBride initially tried to raise his concerns internally with the Australian Defence Force (ADF), but became unsatisfied with the process, so he set up a website and uploaded a trove of secret documents.

Former military lawyer David McBride
When ADF officials found the website containing classified material, they wrote to McBride reminding him of his duty not to disclose it, prompting him to take it down. No action was taken against McBride for his website leak and the Court noted in sentencing that those leaks gave rise to very little risk.
It was only after McBride leaked the material to ABC journalists who aired them in the ‘Afghan Files’ story alleging Australian soldiers did ‘kill people unnecessarily’ that McBride was arrested, interviewed and charged.
Federal police raided the ABC’s Sydney headquarters in 2019, searching for evidence of a leak, but decided against charging the journalists.
In 2023, McBride pleaded guilty to several charges, including stealing secret classified military documents and leaking them to journalists. However McBride couldn’t rely on those documents in his legal defence when the Australian government stopped them from being adduced as evidence on national security grounds.
McBride argued there was a “culture of cover-up” at the command level of the Australian Army. While most soldiers acted ethically, he said some were needlessly investigated and others were protected after allegedly, “put(ting) a gun to someone’s head and blow(ing) their head away” even if they were unarmed or handcuffed.
McBride says he felt a moral obligation to bring these issues to light, believing the Australian public deserved to know the truth about their country’s military actions.
The years-long legal battle which has now landed McBride in prison, has sparked acrimonious debates about the need for an independent Whistleblower Protection Authority in Australia, and the media’s vital role in making powerful institutions accountable.
Human rights whistleblower lawyers said McBride’s punishment sends a chilling message to potential whistleblowers. They contend the Australian government should protect those who expose wrongdoing, not punish them.
Critics argued, however, that McBride was entitled and self-interested. Prosecutors suggested McBride had abandoned the internal investigation he initiated without waiting for the result, violated his signed confidentiality acknowledgments as a military lawyer, and compromised the lives of soldiers and their families while potentially harming Australia’s national security and international relations.
The Brereton Inquiry, commenced by the ADF before McBride’s whistleblowing leaks, found credible information that Australian Special Forces had unlawfully killed people in Afghanistan.
It also appears no harm has been demonstrated because of McBride’s actions, though the ACT Supreme Court said in sentencing, that potential harm to Australia’s defence personnel, their families, Australia’s national security and international relations, still exists.
In sentencing McBride, ACT Supreme Court Justice David Mossop said that while he was a person of good character strongly devoted to duty, from his time in Afghanistan he was unable to accept that his opinions about the ADF may be incorrect.
Justice Mossop considered McBride knew he was committing a criminal offence when disclosing the information but hoped he would have a (public interest) defence. McBride had legal duties and constraints as a soldier and lawyer serving the Army, but no specific duty to disclose the secret information to outsiders when there were other legitimate ways he could have raised his concerns.

ACT Supreme Court Justice David Mossop
Justice Mossop also said McBride had no remorse and still believed he did the right thing, so he sentenced McBride to prison to deter him from disclosing anymore military information and to deter other people ‘with strong opinions’ who are also under a legal duty not to disclose information, from doing so.
McBride abandoned his defence of a higher duty to act in the public interest even if it involves disobeying orders, when the Court ruled this out. Yet he remained defiant, justifying his actions saying, “I served my country. I stand tall and I believe I did my duty and I see this as a beginning to a better Australia.”
In the lead up to his sentencing, he added “So long as people believe I stood up for what I believed in, I can go to jail with my head held high.”
Independent MP Andrew Wilkie was outraged by McBride’s prison sentence, saying that governments “hate people shining a light on official misconduct.”
He added, “They consistently want to punish the whistleblower, and they consistently want to send a signal to would be whistleblowers to shut up, to not break ranks, to not cause problems for governments.”

AAP: Independent MP Andrew Wilkie
Daniela Gavshon, Australian Director of Human Rights Watch, said McBride’s sentencing shows that Australia’s whistleblowing laws need exemptions in the public interest.
“It is a stain on Australia’s reputation that some of its soldiers have been accused of war crimes in Afghanistan, and yet the first person convicted in relation to these crimes is a whistleblower not the abusers,” Gavshon said in a statement.
Many regard whistleblowing as morally courageous, especially when done in the public interest, as McBride claimed he did. But whistleblowing is a dangerous endeavour in Australia because of the significant legal and personal risks.
Compared to the US, where whistleblower protections are considered more robust, McBride’s case demonstrates the protracted and costly legal battles faced by whistleblowers in Australia, when up against institutions with unlimited resources.
It’s now feared McBride’s prosecution and sentencing will deter other whistleblowers from disclosing information because Australia’s laws arguably do not protect whistleblowers like McBride, who try internal reporting channels first but then find them inadequate.
While there must be a balance between national security concerns and the public’s right to know about the actions of their government and military, McBride’s case means other Australians thinking about whistleblowing, risk imprisonment too, especially where there is low trust in internal reporting channels and no alternative external reporting channel.
Australia’s Government has already announced plans to bolster public whistleblowing protections. But that won’t help McBride whose imprisonment highlights the urgent need for clear guidance and protection when disclosing information to prevent more serious harms, and the vital need for a free press if and when internal whistleblowing channels, fail.
Prior to being imprisoned, McBride recorded the following video:
Ukraine Prepares Total Mobilization in 5 Controlled Cities – Russian Official
Sputnik – 15.05.2024
SIMFEROPOL – Kiev is preparing full-scale mobilization in five Ukrainian-controlled cities in the coming days, Vladimir Rogov, a senior official of the Russia-appointed Zaporozhye regional administration, told Sputnik on Wednesday.
“According to the received operational information, [the cities of] Kostyantynovka, Slovyansk, Pavlograd, Zaporozhye, Kharkov should be subjected to total mobilization in the coming days. We are talking about the complete blocking of roads in the cities with checkpoints, filtration measures, apartment and house-to-house rounds. Everything is expected to start on May 17-18,” Rogov said.
He added that hundreds of employees of the Ukrainian military recruitment centers were coming in the cities to collect people, with reinforcements from the Ukrainian National Guard and the Ukrainian Security Service.
On April 11, the Ukrainian parliament adopted a bill on mobilization aimed at replenishing Ukrainian forces depleted by two years of armed conflict with Russia. On April 16, Ukrainian President Volodymyr Zelensky signed it into law. The document will take effect on May 18.
Martial law was introduced in Ukraine on February 24, 2022. The next day, Zelensky signed a decree on general mobilization. The martial law and mobilization have been continuously extended since then. On May 9, Zelensky signed bills to extend mobilization and martial law in the country for another 90 days. Under martial law, men aged from 18 to 60 are prohibited from leaving Ukraine.
Meta’s Oversight Board Adopts International “Norms” Instead of US Free Speech Principles
By Didi Rankovic | Reclaim The Net | May 14, 2024
In a world where international law (a set of ratified documents) is being rapidly replaced with narratives about a “rules-based system,” it is no wonder that US tech giants like Meta choose to set their free speech “baseline” not on their country’s Constitution, but on “international human rights norms.”
The less clarity there is, the more space for abuse and biased interpretation, critics might say. But Meta Oversight Board member Kenji Yoshino is satisfied that this is the right approach, and even spelled it out.
“Our baseline here is not the US Constitution and free speech, but rather international human rights norms,” Yoshino recently told the National Constitution Center, a private nonprofit.
Such bold statements require bold justification, and so this Oversight Board member noted that in terms of free speech “values” the US is “an outlier,” while Meta’s global reach means it must adjust its policies accordingly.
There are plenty of openly authoritarian regimes out there, with their own “free speech values,” but when Yoshino – from the William J. Brennan Center for Justice – spoke about “striking a balance” between US law and international “norms” – he chose to mention the palatable to his audience example of Europe.
What’s striking in this context, however, is that in many, if not all European countries, “hate speech” is criminalized, unlike in the US. It isn’t clear from Yoshino’s statements how a balance between such different approaches to speech can even be achieved in a social platform’s guidelines, particularly around elections.
But, that is the explanation for why the giant chooses not to make the First Amendment its “baseline.”
And if the baseline is international human rights norms, Yoshino admitted, “often times that calculus comes out differently than it would if the baseline were First Amendment norms.”
Such statements will do little to reassure those in the US already wary of Meta’s handling of content, censorship, and free speech, especially ahead of yet another high-stakes election coming up.
The fact that after a brief “pause” the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) are now officially back in the business of “communicating” (opponents of the policy would say, “colluding”) with social media platforms, doesn’t help matters.
If anything, it raises fears of a concerted censorship push, driven both from the outside by government pressure, and from within Meta itself.
